Relationships with the Firewall Service and Security Group Function
If a firewall is enabled on a virtual router, the relationship with the firewall is as shown below. Although the Allow rules for the SSL-VPN connection are automatically added, you must explicitly configure the firewall service to allow communication such as SSH communication for logging in to a virtual server.
- You can configure security group settings for SSL-VPN Connection resources. If you do not configure a security group, the service will automatically use a security group that does not block communication.
- For "Example 2: Configuration using the same network for services and maintenance", set rules allowing communication from both networks on the firewall and security groups.
An image of the configuration when using the firewall service and the security group function is shown below.
Figure: Image of SSL-VPN Communication
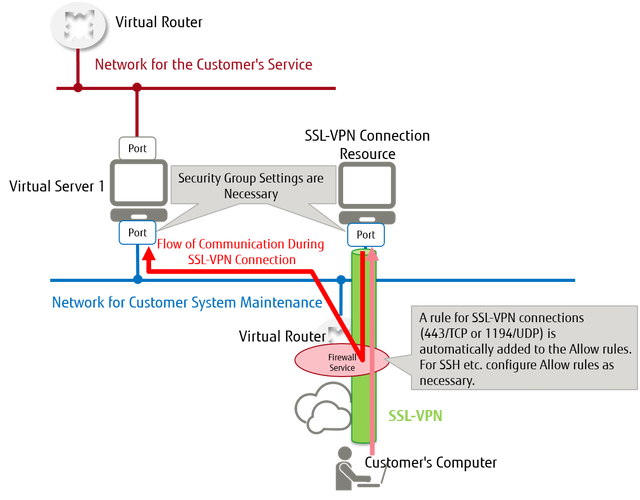
When using the firewall service, the following Allow rules are necessary.
- Firewall Rules for an SSL-VPN Connection
- Firewall Rule for Communication after It Passed an SSL-VPN Connection
Firewall Rules for an SSL-VPN Connection
If you create the SSL-VPN Connection resource when a firewall service has already been created, a firewall rule (443/TCP or 1194/UDP) where 'Source IP Address' is set to 'Omit' will automatically be added.
If you create a firewall service after creating an SSL-VPN Connection resource, add this rule manually.
| Source IP Address | Source Port Number | Destination IP Address | Destination Port Number | Protocol |
|---|---|---|---|---|
| Your computer's IP address (SSL-VPN client) | Omit | IP address of SSL-VPN Connection resources *1 | 443 or 1194 *2 | tcp or udp *2 |
*1: This is the value specified for 'internal_gateway' on the SSL-VPN Connection resource.
*2: Selected according to the protocol type specified for the SSL-VPN Connection. When setting this manually, set according to the protocol type.
-
If the protocol type is 'tcp'
- Destination Port Number: 443
- Protocol: tcp
-
If the protocol type is 'udp'
- Destination Port Number: 1194
- Protocol: udp
Firewall Rule for Communication after It Passed an SSL-VPN Connection
Add a rule to explicitly permit communication after it passed an SSL-VPN Connection.
| Source IP Address | Source Port Number | Destination IP Address | Destination Port Number | Protocol |
|---|---|---|---|---|
| Client Address Pool CIDR for SSL-VPN *3 | Omit | Virtual server (connection destination server) | Communication protocol used for communication after it passed an SSL-VPN Connection *4 | Communication port number used for communication after it passed an SSL-VPN Connection *4 |
*3: The virtual network CIDR (client_address_pool_cidr) used by the SSL-VPN client of the SSL-VPN Connection resource. For details, refer to "Create SSL VPN V2 Connection" in the "API Reference - Network".
*4: For example, to make an SSH connection to a virtual server, specify the following:
- Destination Port Number: 22
- Protocol: tcp
Security Group Rule for the SSL-VPN Connection
When you configure a security group, the following Allow rule is necessary.
| Direction | Communication Partner | Protocol | Starting Port No. | Ending Port No. |
|---|---|---|---|---|
| Inbound (Ingress) | Your computer (SSL-VPN client) | tcp or udp *1 | 443 or 1194 *1 | Same value as the one that you specified for the starting port number |
| Outbound (Egress) *2 | Virtual server (connection destination server) | Communication protocol for communication after it passed the SSL-VPN Connection | Communication port number for communication after it passed the SSL-VPN Connection | Same value as the one that you specified for the starting port number |
*1: Select according to the protocol type specified for the SSL-VPN Connection.
-
If the protocol type is 'tcp'
- Protocol: tcp
- Starting Port Number: 443
- Ending Port Number: 443
-
If the protocol type is 'udp'
- Protocol: udp
- Starting Port Number: 1194
- Ending Port Number: 1194
*2: According to the default rule that is created at the time when you create a security group, all communication in the outbound direction is allowed. To explicitly restrict communication in the outbound direction, delete the default rule and add this rule.
*3: For example, to make an SSH connection to a virtual server, specify the following:
- Protocol: tcp
- Starting Port Number: 22
- Ending Port Number: 22