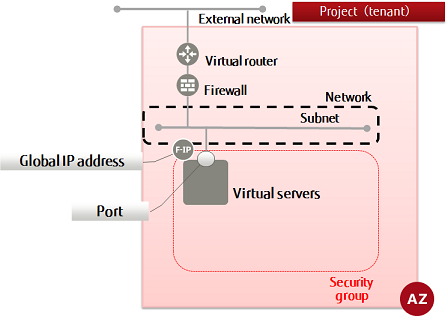
Security groups allow you to group, define and configure rules to filter packets for ports that virtual servers are connected to. Follow the procedure below to create a security group.
You can set multiple rules for a security group. Of the security groups set for a single port, Communication on a port is permitted only for packets that match at least one rule in any one of the security groups assigned to it. All other packets are intercepted. (whitelist method, OR condition)
Note: Security groups cannot be set for ports used by a virtual router or DHCP server.
A default security group that automatically intercepts communication is set for ports. To permit communication, create a security group.
-
Set the environment variable below as follows:
Security groups are not associated with availability zones, and therefore, it is not necessary to specify one.
$ SG_NAME=<newSecGroupName> (any)
-
Execute the following API:
$ curl -Ss $NETWORK/v2.0/security-groups -X POST \
-H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type: application/json" \
-d '{"security_group": {"name": "'$SG_NAME'"}}' | jq .
The following response is output:
{
"security_group": {
"tenant_id": "<projId>",
"description": "",
"name": "<newSecGroupName>",
"security_group_rules": [
{
"remote_group_id": null,
"direction": "egress",
"remote_ip_prefix": null,
"protocol": null,
"ethertype": "IPv6",
"port_range_max": null,
"security_group_id": "<newSecGroupId>",
"port_range_min": null,
"tenant_id": "<projId>",
"id": "<defaultSecGroupRuleId>"
},
{
"remote_group_id": null,
"direction": "egress",
"remote_ip_prefix": null,
"protocol": null,
"ethertype": "IPv4",
"port_range_max": null,
"security_group_id": "<newSecGroupId>",
"port_range_min": null,
"tenant_id": "<projId>",
"id": "<defaultSecGroupRuleId>"
}
],
"id": "<newSecGroupId>"
}
}
-
List the security groups to confirm that it has been created.
$ curl -Ss $NETWORK/v2.0/security-groups -X GET \
-H "X-Auth-Token: $OS_AUTH_TOKEN" | \
jq '.security_groups[]| .name, .description, .id'
If a list including the security group name that you specified is output, as follows, that means the security group was created successfully.
"default"
"default"
"<defaultSecGroupIdOfProj>"
...
"<newSecGroupName>"
""
"<newSecGroupId>"
...