Creating an SSL-VPN connection (V2 service/K5 client certificate)
This section explains the procedure for creating a (V2 service) SSL-VPN connection.
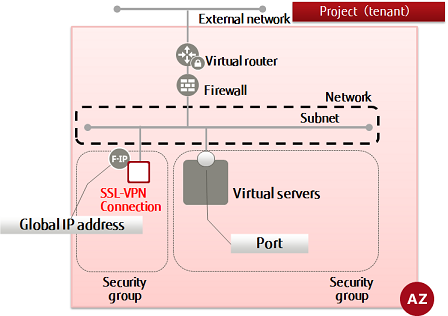
-
Execute the following commands to perform the necessary configuration.
$ NAME=<Connection Name (Optional)>
$ VPNSERVICE_ID=<VPN Service ID>
$ PROTOCOL=tcp
$ AZ=<Availability Zone>
$ CLIENT_ADDRESS_POOL_CIDR=<Virtual Network cidr of VPN Tunnel (Optional)>
For "CLIENT_ADDRESS_POOL_CIDR", specify the network address using the format XXX.XXX.XXX.XXX/XX.
Example: 192.168.246.0/24
Warning:Specify a network address that does not conflict with the network address used by K5 or the local network addresses used by client PCs.
Note:When an SSL-VPN connection is created using this procedure, the following settings are configured automatically.
- Firewall rules
A firewall rule (443/TCP) allowing access to the SSL-VPN connection is added automatically for use during dedicated SSL-VPN connections.
When you want to change the firewall rules that are added automatically, make changes after creating the SSL-VPN connection.
- Static routing information
The routing information to "client_address_pool_cidr" configured in the SSL-VPN connection is added to virtual routers for use during dedicated SSL-VPN connections.
- Security groups
A security group in which permissions for all types of communication are configured is created for use during dedicated SSL-VPN connections.
It is also possible to use a security group that has been created by a user by specifying it in the "security_groups" parameter when creating the SSL-VPN connection.
For details, refer to the "Fujitsu Cloud Service K5 IaaS API Reference - Network".
- Global IP address
If the "floatingips" parameter is not specified, a global IP address to be allocated to the SSL-VPN connection is generated.
When using a global IP address that has been generated in advance, specify the "floatingips" parameter.
For details, refer to the "Fujitsu Cloud Service K5 IaaS API Reference - Network".
Note:In addition to the settings that are configured automatically, it is necessary to define permissions in the security groups and firewall rules so that the virtual network that is configured in the "client_address_pool_cidrs" parameter of the SSL-VPN connection can access the connection destination virtual server.
- Firewall rules
-
Execute the following API.
$ curl -sS $NETWORK/v2.0/vpn/ssl-vpn-v2-connections -X POST \ -H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type: application/json" \ -d '{"ssl_vpn_v2_connection": {"name": "'$NAME'", "client_address_pool_cidrs": [ "'$CLIENT_ADDRESS_POOL_CIDR'" ] , "admin_state_up": true, "vpnservice_id": "'$VPNSERVICE_ID'", "availability_zone": "'$AZ'", "protocol": "'$PROTOCOL'"} }' | jq .The following response will be returned.
{ "ssl_vpn_v2_connections": [ { "access_points": [ { "floatingip": null, "client_address_pool_cidr": "<Virtual Network cidr of VPN Tunnel>", "internal_gateway": "<Private IP Address for SSL-VPN Connection>", "external_address": "<Global IP Address for SSL-VPN>" } ], "security_groups": [ "<Dedicated Security Group for SSL-VPN Connection>" ], "protocol": "tcp", "availability_zone": "<Availability Zone>", "tenant_id": "<Project ID>", "name": "<SSL-VPN Connection Name>", "admin_state_up": true, "client_address_pool_cidrs": [ "<Virtual Network cidr of VPN Tunnel>" ], "credential_id": null, "vpnservice_id": "<VPN Service Name>", "id": "<SSL-VPN Connection ID>", "status": "PENDING_CREATE" } ] } -
Execute the following API to confirm the status of the SSL-VPN
connection.
$ curl -sS $NETWORK/v2.0/vpn/ssl-vpn-v2-connections -X GET \ -H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type:application/json" \ | jq .
Confirm that the "status" of the SSL-VPN connection is "ACTIVE" as shown in the following response.
{ "ssl_vpn_v2_connections": [ { "access_points": [ { "floatingip": null, "client_address_pool_cidr": "<Virtual Network cidr of VPN Tunnel>", "internal_gateway": "<Private IP Address for SSL-VPN Connection>", "external_address": "<Global IP Address for SSL-VPN>" } ], "security_groups": [ "<Dedicated Security Group for SSL-VPN Connection>" ], "protocol": "tcp", "availability_zone": "<Availability Zone>", "tenant_id": "<Project ID>", "name": "<SSL-VPN Connection Name>", "admin_state_up": true, "client_address_pool_cidrs": [ "<Virtual Network cidr of VPN Tunnel>" ], "credential_id": null, "vpnservice_id": "<VPN Service Name>", "id": "<SSL-VPN Connection ID>", "status": "ACTIVE" } ] }Immediately after creation, in some cases the status may still be PENDING_CREATE. In such cases, wait a while and then execute the confirmation API again.
-
Execute the following API to confirm the status of the VPN service.
$ curl -sS $NETWORK/v2.0/vpn/vpnservices -X GET \ -H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type:application/json" \ | jq .
If the "status" of the VPN service is "ACTIVE" as shown in the following response, then creation of the SSL-VPN connection is complete.
{ "vpnservices": [ { "availability_zone": "<Availability Zone>", "router_id": "<Router ID for SSL-VPN Connection>", "status": "ACTIVE", "name": "<VPN Service Name>", "admin_state_up": true, "subnet_id": "<Subnet ID for SSL-VPN Connection>", "tenant_id": "<Project ID for SSL-VPN Connection>", "id": "<VPN Service ID>", "description": "" } ] }