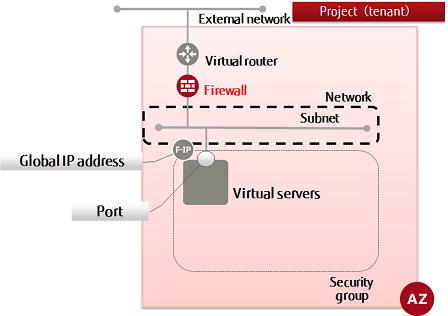
This section explains how to specify a firewall policy (for which rules have been registered) to create a firewall for a virtual router.
The firewall service settings comprise the following elements, with the filtering information being configured in number order. By associating a firewall with a virtual router, the specified filtering will be performed.
- Create firewall rules
- Create a firewall policy and register rule groups
- Specify a policy, create a firewall, and associate it with the virtual router
-
Set the environment variables below as follows:
$ FW_NAME=<newFirewallName> (any)
$ FWP_ID=<firewallPolicyIdToBeSet>
$ ROUTER_ID=<virtualRouterIdToBeApplied>
$ AVAILABILITY_ZONE=<sameAvailabilityZoneAsSetInTheFirewallPolicy>
-
Execute the following API:
$ curl -X POST -Ss $NETWORK/v2.0/fw/firewalls \
-H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type: application/json" \
-d '{"firewall": {"name": "'$FW_NAME'",
"firewall_policy_id": "'$FWP_ID'", "router_id": "'$ROUTER_ID'",
"availability_zone": "'$AVAILABILITY_ZONE'"}}' | jq .
The following response is output:
{
"firewall": {
"status": "PENDING_CREATE",
"router_id": "<specifiedVirtualRouterId>",
"name": "<newFirewallName>",
"admin_state_up": true,
"tenant_id": "<projId>",
"firewall_policy_id": "<specifiedFirewallPolicyId>",
"id": "<newFirewallId>",
"description": "",
"availability_zone": "<availabilityZone>"
}
}
For the availability zones, AZ1 is expressed as "jp-east-1a", and AZ2 is expressed as "jp-east-1b".
-
Execute the following API to check the firewall that you created:
$ curl -X GET -Ss $NETWORK/v2.0/fw/firewalls \
-H "X-Auth-Token: $OS_AUTH_TOKEN" | jq .
If a list including the firewall policy names that you specified is output, as follows, that means the firewall policies were created successfully.
{
"firewalls": [
...
{
"status": "PENDING_CREATE",
"router_id": "<specifiedVirtualRouterId>",
"name": "<newFirewallName>",
"admin_state_up": true,
"tenant_id": "<projId>",
"firewall_policy_id": "<specifiedFirewallPolicyId>",
"id": "<newFirewallId>",
"description": "",
"availability_zone": "<availabilityZone>"
},
...
]
}
Warning:
If a firewall policy or rules outside of your project are set, the created firewall will not work properly. When this state occurs, deletions by the user will no longer be possible, and it will be necessary for the K5 platform administrator to perform deletions. Create the firewall and its policies/rules so that they have the same project ID.