Creating a firewall rule (IP address specification)
This section explains how to create a firewall rule (IP address specification) to use the firewall service for setting packet filters for virtual routers
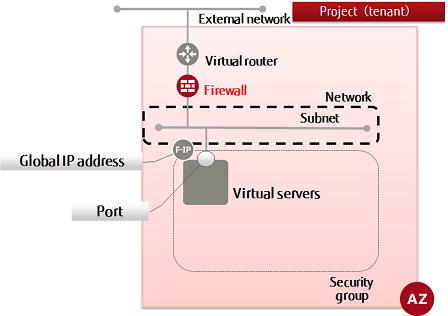
All traffic is intercepted by default (whitelist format), and only traffic that is defined using permission rules (AC=allow) passes through the firewall.
- Create firewall rules
- Create a firewall policy and register rule groups
- Specify a policy, create a firewall, and associate it with the virtual router
Configure the settings as below to create firewall rules.
- The source or destination IP address
- The protocol to use for communication
- The port number to use for communication
- Whether to allow or deny communication
This item explains how to create specific rules such as those shown below.
- Allow: Source IP address: TCP
- Allow: Source IP address: UDP
- Allow: Source IP address: ICMP
While you can do advanced settings for a firewall, this guide shows how to create commonly used rules. Refer to the Service Specification and API Reference Manual for details on the advanced setting items and how to configure them.
When finished creating firewall rules, proceed with creation of a firewall policy to which those rules are bound.