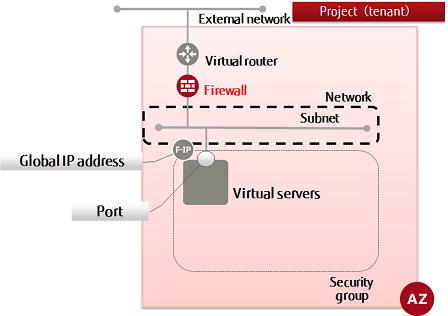
This section explains how to create a firewall rule (port number specification) to use the firewall service for setting packet filters for virtual routers.
Tip: The firewall service settings comprise the following elements, with the filtering information being configured in number order. By associating a firewall with a virtual router, the specified filtering will be performed.
All traffic is intercepted by default (whitelist format), and only the traffic that is defined using permission rules (AC=allow) passes through the firewall.
- Create firewall rules
- Create a firewall policy and register rule groups
- Specify a policy, create a firewall, and associate it with the virtual router
This items explains how to create specific rules such as those shown below.
- Allow: SSH (TCP: 22)
- Allow: HTTP (TCP: 80)
- Allow: HTTPS (TCP: 443)
- Allow: NTP (UDP: 123)
- Allow: KMS (TCP: 1688)
- Allow: RDP (TCP: 3389)
While you can do advanced settings for a firewall, this guide shows how to create commonly used rules. Refer to the Service Specification and API Reference Manual for details on the advanced setting items and how to configure them.
-
Set the environment variables below as follows:
$ FWR_NAME=<firewallRuleName> (any)
$ AC=<accessControl> (allow)
$ DESTINATION_PORT=<destinationPortNumOrRange> (for example, "0 - 255", 22, etc.)
$ PROTOCOL=<protocol> (specify tcp, udp, icmp)
$ AVAILABILITY_ZONE=<creationDestinationAvailabilityZoneName>
-
Execute the following API:
$ curl -X POST -Ss $NETWORK/v2.0/fw/firewall_rules \
-H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type: application/json" \
-d '{"firewall_rule": { "name": "'$FWR_NAME'" , "action": "'$AC'",
"destination_port": "'$DESTINATION_PORT'" , "protocol": "'$PROTOCOL'",
"availability_zone": "'$AVAILABILITY_ZONE'" }}' | jq .
The following response is output:
{
"firewall_rule": {
"protocol": "<protocol>",
"description": "",
"ip_version": 4,
"tenant_id": "<projId>",
"enabled": true,
"source_ip_address": "null",
"destination_ip_address": null,
"firewall_policy_id": null,
"action": "allow",
"shared": false,
"source_port": null,
"position": null,
"destination_port": "<specifiedPortNum>",
"id": "<newFirewallRuleId>",
"name": "<newFirewallRuleName>",
"availability_zone": "<specifiedAvailabilityZone>"
}
}
For the availability zones, AZ1 is expressed as "jp-east-1a", and AZ2 is expressed as "jp-east-1b".
-
Execute the following API to check the firewall rules that you created:
$ curl -Ss $NETWORK/v2.0/fw/firewall_rules -X GET \
-H "X-Auth-Token: $OS_AUTH_TOKEN" | jq '.firewall_rules[] | .name,.id'
If a list including the firewall rule names that you specified is output, as follows, that means the firewall rules were created successfully.
...
"<newFirewallRuleName>"
"<newFirewallRuleId>"
...
When finished creating firewall rules, proceed with creation of a firewall policy to which those rules are bound.