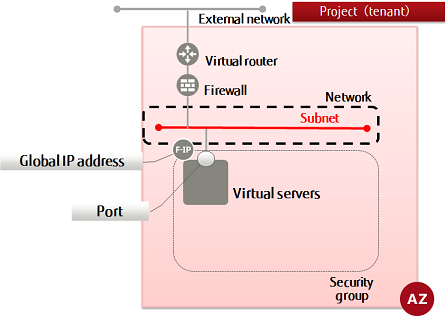
Creating a subnet
A subnet is required for managing private IP addresses for resources to be connected to a network, and for automatic setting of IP addresses using DHCP. This section explains how to create a subnet and then check that it was created properly.
Specify a network and create a subnet.
-
Set the environment variables below as follows:
Note:
This procedure sets up a DNS server, but for a virtual server to communicate with the DNS server, it is necessary to allow outbound communication to the Internet. Check the settings of the security group feature or firewall service, and allow communication with the DNS server (protocol: TCP/UDP, port number: 53).
Note that the value specified for DNS will vary depending on the environment. When using the DNS provided by the K5 IaaS, refer to the appendix "Common Network Services" in the "Features Handbook".
$ SUBNET=<newSubnetName> (any)
$ NETWORK_ID=<networkId>
$ CIDR=<networkAddr> (any, using format XXX.XXX.XXX.0/24)
$ GATEWAY_ID=<defaultGatewayIpAddr> (any, using format XXX.XXX.XXX.1)
$ DNS=\"133.162.XXX.XXX\"\,\"133.162.XXX.XXX\"
Note:For the range of addresses specifiable for the CIDR parameter, refer to "Subnet Management" in the "Features Handbook".
Specify any desired IP address within the address range specified for the CIDR parameter for the GATEWAY_IP parameter.
Warning:For the created subnet, if connecting using an SSL-VPN connection (the V2 service), it is necessary to specify the following values for the variables above.
- CIDR
Specify the mask value for the network address in the range of "16bit - 29bit".
Example: 192.168.1.0/24
- GATEWAY_IP
Specify the IP address of the virtual router specified for the VPN service.
- CIDR
-
Execute the following API:
$ curl -Ss $NETWORK/v2.0/subnets -X POST \ -H "X-Auth-Token: $OS_AUTH_TOKEN" -H "Content-Type: application/json" \ -d '{"subnet": {"name": "'$SUBNET'", "network_id": "'$NETWORK_ID'", "cidr": "'$CIDR'", "dns_nameservers": ['$DNS'], "ip_version": 4, "gateway_ip": "'$GATEWAY_IP'", "availability_zone": "'$AZ'"}}' | jq .The following response is output:
{ "subnet": { "name": "<newSubnetName>", "enable_dhcp": true, "network_id": "<specifiedNetworkId>", "tenant_id": "<projId>", "dns_nameservers": [ "133.162.XXX.XXX", "133.162.XXX.XXX" ], "allocation_pools": [ { "start": "XXX.XXX.XXX.2", "end": "XXX.XXX.XXX.254" } ], "host_routes": [], "ip_version": 4, "gateway_ip": "<specifiedDefaultGatewayIpAddr>", "cidr": "<specifiedNetworkAddr>", "id": "<newSubnetId>", "availability_zone": "<sameAvailabilityZoneAsSpecifiedNetwork>" } }For the availability zones, AZ1 is expressed as "jp-east-1a", and AZ2 is expressed as "jp-east-1b".
-
Execute the following API to check that the subnet was created properly.
$ curl -Ss $NETWORK/v2.0/subnets -X GET \ -H "X-Auth-Token: $OS_AUTH_TOKEN" | jq .
A response is output in a format such as the following. If a list including the subnet name that you specified is output, that means the subnet was created successfully.
Subnets with names that begin with "inf_az1_fip-pool", "inf_az2_fip-pool", "inf_az1_ext-subnet", and "inf_az1_ext-subnet", are associated with external networks that exist by default.
{ "subnets": [ ... { "name": "<subnetName>", "enable_dhcp": true, "network_id": "<networkId>", "tenant_id": "<projId>", "dns_nameservers": [ "133.162.XXX.XXX", "133.162.XXX.XXX" ], "allocation_pools": [ { "start": "XXX.XXX.XXX.2", "end": "XXX.XXX.XXX.254" } ], "host_routes": [], "ip_version": 4, "gateway_ip": "<defaultGatewayIpAddr>", "cidr": "<networkAddr>", "id": "<subnetId>", "availability_zone": "<sameAvailabilityZoneAsNetwork>" }, ... ] }