System structure diagram
This section explains the system structures that can be created.
When releasing a virtual server on the Internet
This section describes the basic procedure in the K5 IaaS for configuring a system that will be released on the Internet.
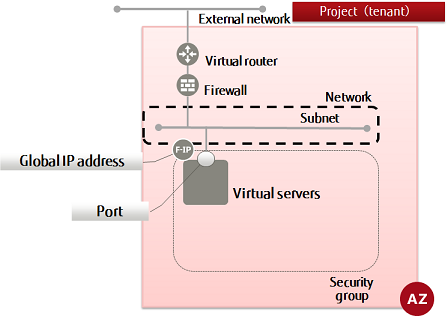
Perform the following tasks in the K5 IaaS to create the system structure.
- Creating a network
- Creating a subnet
- Creating a virtual router
- Changing the information of a virtual router (attaching to an external network)
- Changing the information of a virtual router (attaching to a subnet)
- Creating a security group
- Creating a security group rule
- Create firewall rules
- Creating a firewall policy
- Creating a firewall
- Creating a key pair
- Creating a port(when creating a virtual server by specifying a port)
- Create a virtual server
- Retrieving a global IP address and assigning it to a virtual server
When using the SSL-VPN connection function
This section describes the basic procedure to perform in the K5 IaaS to configure a system that can be connected to over SSL-VPN.
- V2 service method
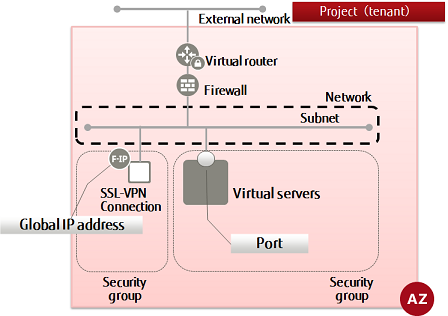
A method in which SSL-VPN connections are established using virtual instances. For details regarding functionality, refer to the "Features Handbook".
There are two user authentication methods that can be used with the V2 service SSL-VPN connection function, "using a K5 client certificate" and "using a self-signed certificate". This document explains the configuration procedure for each user authentication method.
Perform the following tasks in the K5 IaaS to configure the system structure.
- Creating a network
- Creating a subnet
- Creating a virtual router
- Changing the information of a virtual router (attaching to an external network)
- Changing the information of a virtual router (attaching to a subnet)
- Creating a security group
- Creating a security group rule
- Create firewall rules
- Creating a firewall policy
- Creating a firewall
- SSL-VPN connection
- Creating a key pair
- Creating a port(if creating a virtual server on which ports are specified)
- Create a virtual server